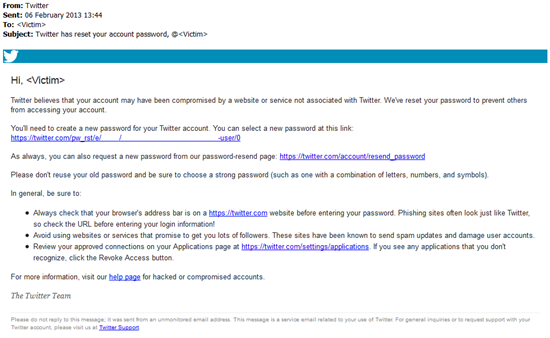
Hot on the heels of Friday’s announcement by Twitter that they ‘detected unusual admission patterns that led to us identifying unauthorized access attempts to Twitter user data’ and subsequent confirmation that ‘attackers may accept had access to limited user information’ for ‘approximately 250,000 users’, Websense® Security Labs™ are tracking a phishing campaign propagated via Twitter’s direct message functionality.
Whilst no correlation betwixt the ii events can be drawn at this time, Twitter users should be on guard for signs of their own business relationship being abused or compromised, as well for abnormal signs or unusual behavior (or peradventure in many cases, more unusual than normal) from those that they follow. Specifically, users should be cautious, as e’er, when post-obit any links received from straight letters or Tweets particularly if the folio you’ve been directed to is asking for your credentials or personal data.
Given the recent compromise, Websense Security Labs suggest that you regularly check your online accounts for signs of compromise and, as if anyone needs an excuse to practise then, regularly update your suitably complex (and most definitely not your pet/team/town or lexicon word) password too as reviewing the permissions granted to 3rd-party applications that have admission to your accounts (Twitter: How to Connect and Revoke Third-Party Applications). Should you lot accept been unlucky plenty to fall victim to this contempo compromise, you’ll take hopefully received a notification from Twitter that suggests these actions forth with some general tips for account security:
Thankfully there are also suggestions, given this recent article on The Guardian’s Web site, that Twitter may be looking to implement two-factor authentication in the future as they are currently advertising a Production Security Software Engineer role in which the successful candidate would have the opportunity to work with “user-facing security features, such as multifactor authentication”. The implementation of 2-factor authentication would exist a welcome addition to Twitter’south service which, based on figures released in 2012, has an estimated 500 million users, of which 200 million are estimated to be ‘active’.
The recent compromise is reported to impact 250,000 users, a mere 0.0005% of total users or 0.00125% of active users, and therefore may seem a somewhat small drib in the Twitter ocean. Information technology is not unsurprising, therefore, that attackers are continuing to target Twitter users by dumping a barrel load of phish into this metaphorical ocean.
This recent phishing entrada, given the samples analyzed by Websense Security Labs and then far in this incident, is using lures likely to elicit a click when received from a friend or acquaintance, such as Did yous meet this pic of you? lolfollowed by a shortened URL.
Interestingly for us, and hopefully you, the utilise of Bitly’southward URL shortening service allows us to append the URL with a plus ‘+’ and and then view statistics for the shortened URL:
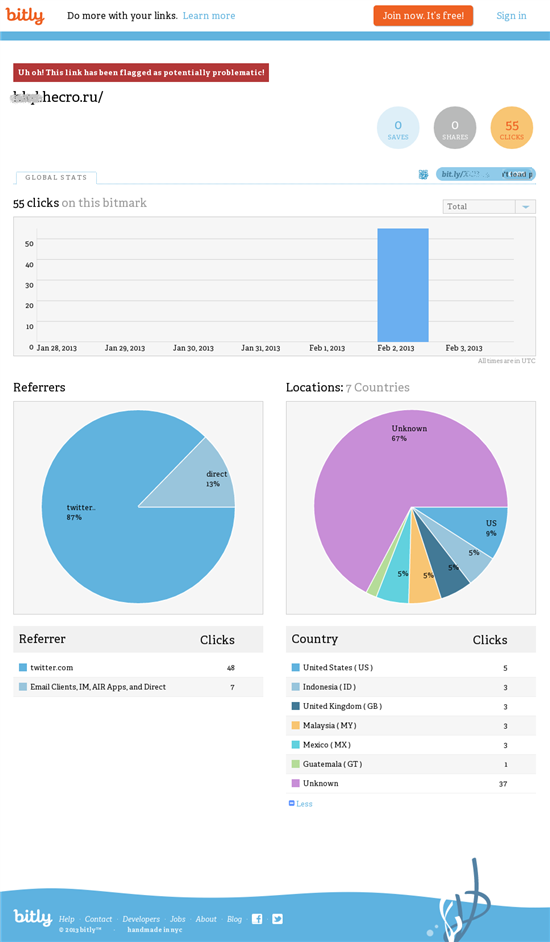
Whilst the click rate for the above instance is low, we’ve seen numerous unique Bitly shortened URLs related to just i business relationship, and would expect the perpetrators behind this campaign to rapidly wheel these in social club to avoid detection and to increase the chances of catching more victims.
From all of the Bitly URLs analyzed, the statistics signal that the victims are not confined to any one geographical area and that users are post-obit the links. With regard to the small percentage of non-Twitter referrers, these could be Tweets or Direct Letters accessed via other applications or indicative that the entrada is non limited to Twitter itself.
Once followed, the shortened URLs atomic number 82 to what appears to exist an intermediate and changing subdomain onhecro(.)ruwhich in turn redirects to active phishing sites hosted on a variety of typosquat-fashion domains:
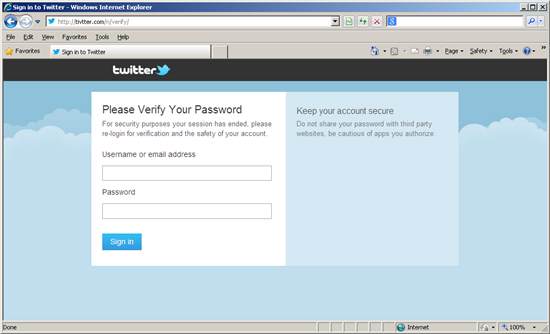
The phishing URL in the to a higher place example,Tivtter(.)com (ACEInsight Study) appears at a glance to be legitimate and therefore is likely to dupe some unsuspecting victims into believing that they need to ‘re-login’ to their expired Twitter session. The URL in this case also appears to bicycle through an alphabetic sequence of folders containing the phishing folio, perhaps in order to gather some statistics or to carve up the campaign in some manner, as we’ve seen active examples from/a/verify/ upwards (/north/verify/ at the fourth dimension of writing). Once the letter has cycled onto the adjacent, any effort to access the phishing page volition be met with a standard ‘404 – Folio not institute’ error.
Should you fill in your account credentials, they’ll exist snaffled by those behind this nefarious scheme and you’ll be presented with a fake ‘404’ page not found fault before being whisked back to the official Twitter Web site as if aught happened:
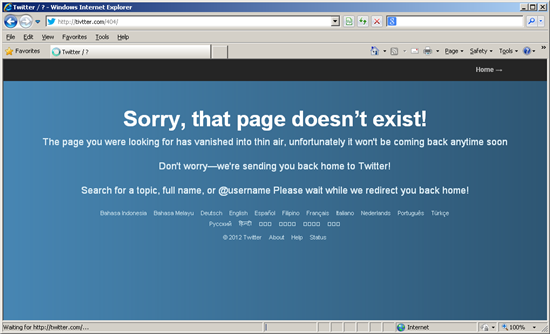
As well every bit the URL above, we’re as well seeing other variations on the same Twitter typo theme includingiftwtter(.)com(ACEInsight Report) andiwltter(.)com (ACEInsight Study).
Reassuringly, Bitly are flagging many of the shortened URLs as ‘potentially problematic’ although it is likely that for every i flagged another is certain to emerge.
Whilst Websense customers are protected from phishing and other threats by ACE, our Advanced Classification Engine, please do ensure that you bank check your personal accounts equally well equally sharing some basic security tips with your friends and family!
[Update] Friday, July xix, 2013:
Websense Labs has been tracking a mutation of this entrada, once again spread via Direct Messaging (DM). The offending domain is a typo-squat – hxxp://twitller(.)com ( Ace Insight Report ), This URL, if browsed to directly, will redirect the visitor to the legitimate https://twitter.com page. However, the URL being DM’d is: hxxp://twitller(.)com/at1/index.php ( Ace Insight Report ) – this page uses xmlHTTP to communicate with a third party web awarding, in club to generate a random URL, similar to hxxp://twitller(.)com/9wk45b/verify/?&account_secure_login – this is where the Phish volition happen, exactly as described in a higher place.
Websense customers are proactively protected from this campaign.
Thanks to @JanneFl for the initial identification of this campaign.
Source: https://www.forcepoint.com/blog/x-labs/battered-twitter-phish-no-chips-updated
 RosyandBo.com Trusted Information and Education News Media
RosyandBo.com Trusted Information and Education News Media