Websense® Security Labs™ researchers, using our Websense ThreatSeeker® Intelligence Cloud, recently noticed an increased employ of custom-generated attachment file names, and some utilize of countersign-protected ZIP files. Emails with cyberbanking/financial themes are being sent with executables packed in Goose egg files, with file names matching the intended recipient. When the attachment runs on a victim’s computer, a Trojan from the Zbot P2P family is downloaded via a Pony loader. Zbot is typically used to steal banking credentials likewise as for the exfiltration of personally identifiable information (PII) and other confidential information for criminal gain. We saw such a entrada on July fifteen, 2013, featuring subjects like “IMPORTANT Docs – WellsFargo” and “IMPORTANT Documents – WellsFargo”. Websense Deject Email Security has detected and blocked over fourscore,000 instances of this campaign. Nosotros have proactively blocked similar cases since June 10. Only as we were getting set up to publish, we have noticed that Websense CES has proactively blocked another campaign, this time using fake emails pretending to be from Trusteer, trying to convince the victim to install an update for Trusteer Rapport software. Again, the attachment names are custom generated to match the recipient’s user name (or the first recipient in the case of multiples). And so far we have blocked more than 36,000 variants of this latest campaign.
Let’s take a look at the campaign from July 15 kickoff:
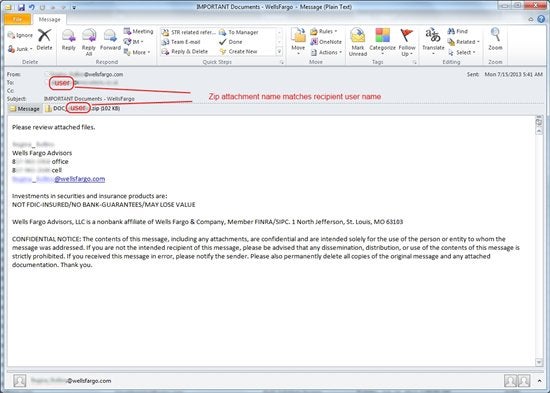
What’due south unique to these campaigns compared with others we take blocked in the past is the custom-generated attachment name. The cyber criminals seem to be trying to come upward with incremental improvements to enhance their effectiveness.
By automating file name cosmos and linking it to the intended recipient’s email username, they are presumably trying to socially engineer the potential victims to feel a little more at ease about opening the attachment. They might also be hoping to become around rudimentary blocking based on zipper file name. In the examples we’ve seen, the packed executable was the same across the same entrada burst. The potential victim first sees the Nix file with their own unique name, so a search for the attachment file name in a search engine might not testify anything suspicious.
A typical misleading icon (another common trait to malware used in email attacks) would cause the file attachment to expect like this if the folder option “Hibernate extensions for known file types” is selected:
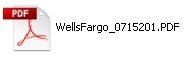
Savvy users will display all file extensions, which will clue them to the suspicious nature of the attachment:
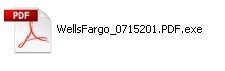
If nosotros analyze the behavior of the zipper using Websense ThreatScope™, nosotros can see the Pony loader module communicates to:
hxxp:// dharmaking.internet/ponyb/gate.php on 64.94.100.116
which is an empty Post transaction in this case, since there was no information to exfiltrate.
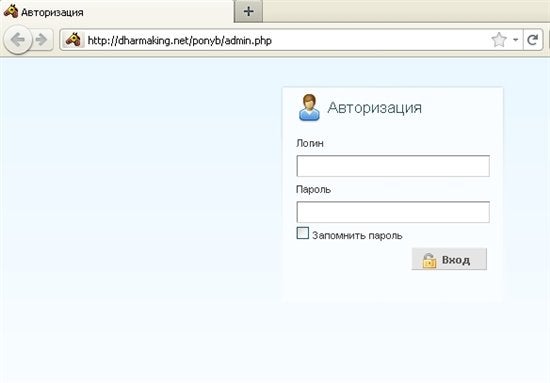
For the sake of curiosity, nosotros can bank check out the admin login panel of the Pony loader on that folio:
The Pony loader sends GET requests to download farther executables from other locations:
hxxp:// liltommy.com/ep9C.exe 184.173.201.131
hxxp:// world wide web.wineoutleteventspace.com/7UNFVh.exe 208.113.243.4
hxxp:// www.oh-onlinehelp.com/Pefyi.exe (suspended, non resolved)
hxxp:// video.wmd-brokerchannel.de/qAz575t.exe 213.148.99.220
Information technology besides includes communication to legitimate sites to mask its malicious activity.
You tin can see the full ThreatScope study hither.
Anti-Virus detection at the time of the attack is pretty dismal, only four out of 45.
Dropped executables are recognized equally malicious past ThreatScope. See reports here and here.
And once more, AV detection is minimal – one out of 47.
But every bit is the case almost of the time, AV vendors eventually update their signatures, and 19 out of 47 now detect the dropped binary as a Zbot Trojan variant.
For comparing sake, we decided to run some other ThreatScope study, to see how our own analytics fared after they had a chance to update.
Here’southward what we found:
Every bit expected, some of the dropped files hosts are not responding anymore. But one really delivered a new binary:
hxxp:// www.wineoutleteventspace.com/7UNFVh.exe
The ThreatScope study indicates that information technology is malicious, as seen here. In add-on, Websense ACE™, our Advanced Classification Engine, had generic detection confronting it.
AV detection? 2 out of 47
We should also notation that ACE updated the categorization of the Uncategorized hosts seen in the initial report:
hxxp:// dharmaking.net/ponyb/gate.php is now nether Bot Networks.
hxxp:// dharmaking.cyberspace/ is at present nether Malicious Web Sites.
hxxp:// www.wineoutleteventspace.com is now under Malicious Web Sites.
See the updated report here.
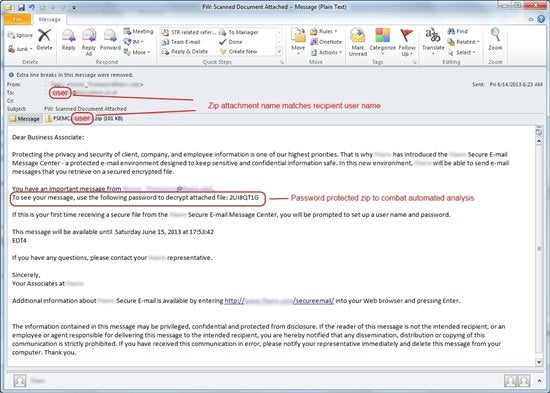
In an older campaign example (June 14, 2013), we can encounter some other feature that has been used frequently in the last few months.
Non merely does the ZIP zipper file name match the recipient’southward user name, information technology is also password protected, with the password supplied in the email body. This is an obvious try to get around automatic analysis and further increase the window of exposure earlier security vendors update their detection for the malware variant.
The attachment (again hiding extensions for known file types) is displayed equally:
![]()
Similar behavior can be seen in the ThreatScope report.
And again, AV is not quite up to speed.
See the dropped executables ThreatScope report, compared to VirusTotal at the time of attack, which is a fiddling better at18 out of 47.
The latest campaign, featuring fake Trusteer emails, has subject lines like:
Important Security Update : Client 9382121
Here’south a sample:
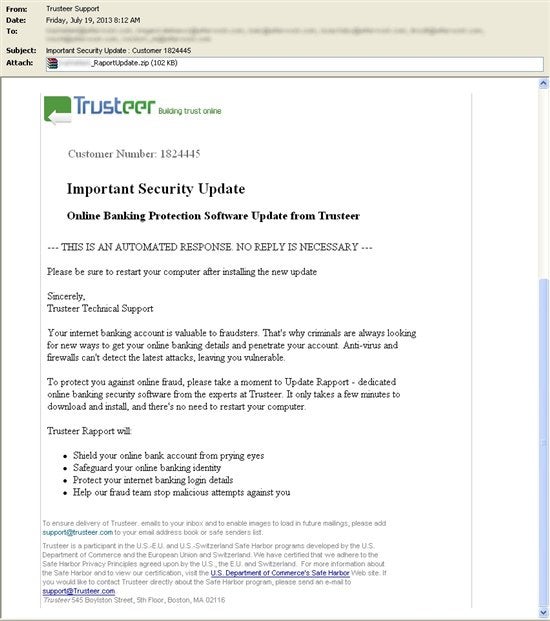
As in the other samples, the attachments are named with a custom generated file proper noun that matches the username of the commencement recipient. Nosotros tin can assume that since Trusteer are a software visitor, the cyber criminals are trying to lure potential victims to exist less suspicious of the executable packed inside the attachment.
Similar beliefs to to a higher place samples, see ThreatScope written report hither, and compare to Virus Full at five/47
Dropped file ThreatScope report, Virus Total at 3/46
It is interesting how simple some of the lures are, but the attackers might be getting enough monetary gain from using them and employing the small, incremental changes described above.
Simple social engineering techniques, known exploits, and known malware families are withal being widely used in attacks large and minor, because apparently they piece of work.
Beyond user education, employing a multi-layered security product that combines multiple analytics could help prevent such attacks.
Websense has provided protection against this campaign in multiple stages. As an email assail carrying attachments, this campaign uses some of the stages outlined in our whitepaper describing the vii stages of Advanced Threats.
Lures – Websense Cloud Electronic mail Security provides proactive protection against emails conveying executables or other suspicious attachments, based on multiple analytics.
Dropper File – Websense ThreatScope recognizes the malicious beliefs of the dropper file.
Call Home – Websense ACE, our Advanced Classification Engine, blocks the Pony loader page via real-time analytics.
Dropped Files – ThreatScope recognizes the malicious behavior of the dropped executable files. In improver, ACE protects confronting the URL hosts.
Data Theft – Websense DLP (information loss prevention) tools can detect and stop the exfiltration of sensitive information, similar the banking credentials and PII that Zbot targets.
Source: https://www.forcepoint.com/blog/x-labs/custom-attachment-names-and-passwords-trojans
 RosyandBo.com Trusted Information and Education News Media
RosyandBo.com Trusted Information and Education News Media