July in Las Vegas isn’t the best time to exist outside, but it is a good time to hear about the latest offensive and defensive moves in the security industry. So again, we headed into the desert for Black Hat 2017 where Opi spent time in sessions and then joined Jim presenting in Forcepoint’s exhibit booth. One of the big trends that Opi noticed was the movement towards security fabrics, with more emphasis on holistic solutions rather than indicate products. We think this will be crucial; it’s part of how Forcepoint will be “protecting the human point” (but more on that another fourth dimension).
Forcepoint did presentations every 15 minutes or then on a variety of topics, including 2 pertaining to network security “Why Evasions Are More Dangerous Than Ever” and “Top 3 Myths nigh Modern Firewalls – Debunked.” Near all of the presentations in our berth had standing room simply (representing several dozen people), including ours.

Advanced evasion techniques seemed to exist of detail involvement to our attendees. These are the ways that attackers manipulate the traffic they transport to hide exploits and malware from network defenses. For example, a payload that is destined for a known vulnerability on a Windows laptop could be broken into pieces and sent out of order:
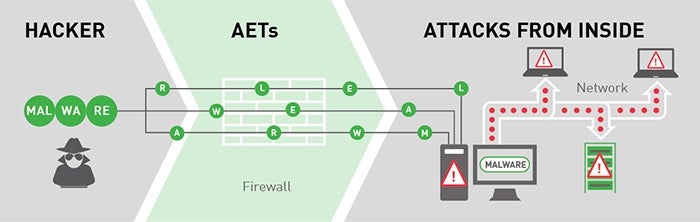
If the firewall in the middle isn’t designed to defeat evasions, it won’t encounter the exploit or the malware payload that would get delivered. (Of class, 1 of the key blueprint elements of Forcepoint’s NGFW is its ability to cake millions of types of evasions.)
Why Evasions are Of a sudden Even More than Relevant
Evasions have become more important than e’er. Recent attacks similar WannaCry and Petya reverberate a new arroyo being taken by cybercriminals. Rather than just relying on social engineering like phishing emails or drive-past downloads from compromised websites, modern attackers are resurrecting older vulnerability (such as the SMB bug that became infamous this jump) ways of getting into networks and propagating. In add-on, they’re combining multiple techniques. Evasions, which are now role of common exploit toolkits, boost the effectiveness of attacks and can help go along them undetected longer, protecting the “investment” the cybercriminals accept made in developing their attacks.
That’s Where Evader past Forcepoint Comes In
To help people understand whether their network security devices are solid or total of evasive holes, nosotros used Black Lid 2017 to begin demonstrating our latest version of Evader. This technology (it’s not a product and we don’t charge for it) provides a ready-made examination lab for subjecting network devices to a wide variety of evasion techniques.

Evader’due south
not
for pentesting or launching arbitrary attacks, but makes it immediately clear when attacks get through. You lot just select which vendor’s device yous wish to examination (we have a multifariousness of them gear up up in a lab with security settings on them plow up to their maximum level of protection):
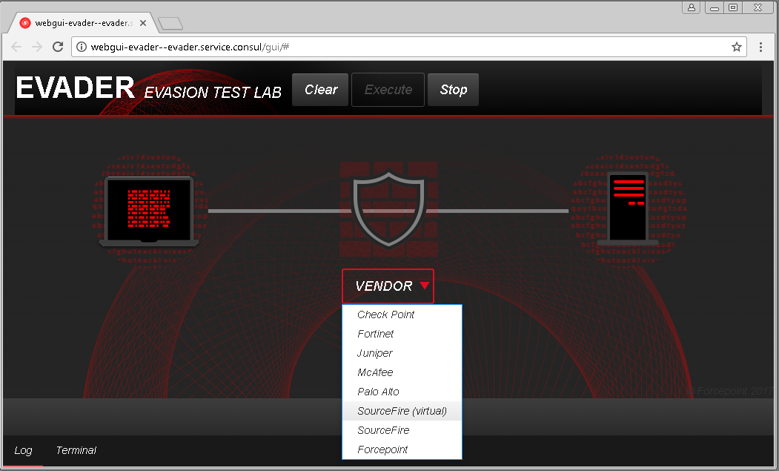
Then select the blazon of evasions and attack yous want to use:
Finally, click “Execute” and spotter the target screen (which is running in a virtual car). Depending upon the assault that was selected, within seconds a successful evasion will cause a window (like a estimator or shell) to announced on the target or the target to bluish-screen.
Evasions are what caused and so many vendors in this year’due south NSS Labs NGFW Test to autumn out of the RECOMMENDED quadrant. NSS has begun ramping up their use of evasions to provide visibility to an result that many vendors seem to otherwise sweep nether the carpet. We’re glad to see them doing it – with attackers combining techniques and using vulnerabilities to spread, evasions leave a huge gap that has to exist filled.
For more data about Evader, or to get your ain live sit-in, please visit the Evader website.
Forcepoint is the leading user and data protection cybersecurity visitor, entrusted to safeguard organizations while driving digital transformation and growth. Our solutions conform in existent-time to how people collaborate with data, providing secure admission while enabling employees to create value.
Source: https://www.forcepoint.com/blog/insights/one-place-where-evasions-couldn-t-hide-evader-black-hat-2017
 RosyandBo.com Trusted Information and Education News Media
RosyandBo.com Trusted Information and Education News Media