Since its introduction the majority of malware authors have shunned .NET as a development platform, despite its relative popularity as a platform for developing legitimate Windows software. There are numerous potential reasons for this, just two in item that likely take a significant influence on malware authors are .Cyberspace lawmaking’s reliance on external libraries (few people are likely to want to install a specific version of the .Net Framework in order to back up someone trying to steal their banking details) and – every bit discussed in the first office of this series – the ease with which information technology can exist decompiled. That said, Forcepoint Security Labs accept seen a measurable increase in the amount of .NET-based malware samples being delivered in the wild during 2017.
Click here for role one of this serial: ‘Security, Operation, Obfuscation & Compression’.
Amanuensis Tesla
In June 2017 Forcepoint Security Labs identified several malicious e-mail campaigns distributing the ‘off the shelf’ Agent Tesla primal logging tool. The capabilities of Agent Tesla accept been well-documented elsewhere, not least by its own authors, and include password recovery tools, the ability to capture the contents of the clipboard, upload screenshots, and – most importantly – the power to obfuscate its ain code through a combination of string encryption (first image, beneath) and dynamically generated role and class names (2d prototype, beneath).
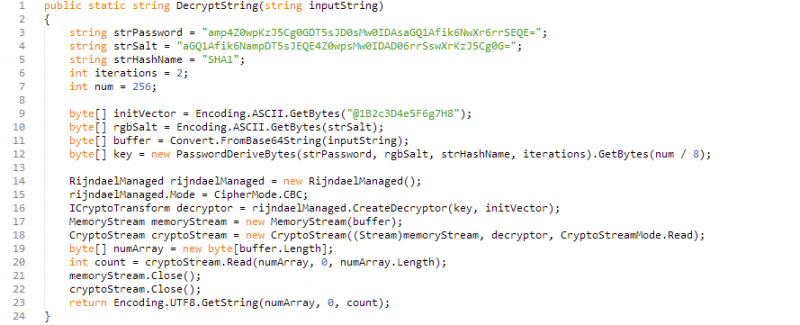
Effigy 1: Agent Tesla’s decryption role
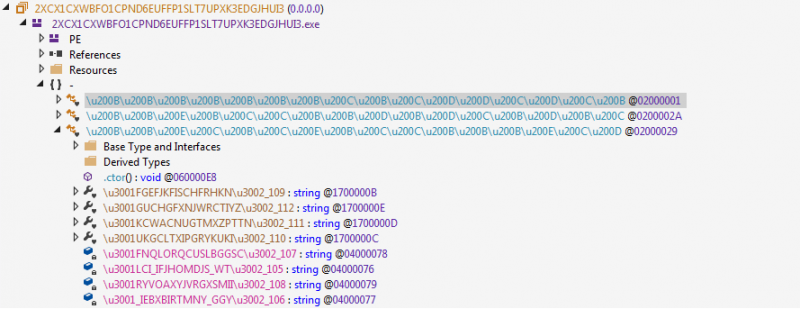
Figure 2: Examples of Amanuensis Tesla’s heavily obfuscated function names
The use of whitespace/unprintable Unicode within the obfuscated class and function names is another common technique to hamper reverse applied science efforts.
The samples shown below were associated with split campaigns and used a multi-stage deployment process wherein an initial executable contains and self-extracts a DLL file which, in turn, performs a similar process to extract and execute the cadre malicious code.
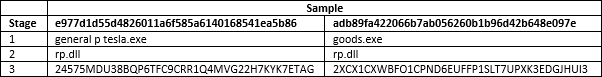
Table 1: ‘Stages’ associated with two Amanuensis Tesla samples captured in June and July 2017, respectively. Notation the consistent naming of the second-phase DLL file.
Much similar obfuscation and encryption, this type of self-extracting deployment process is a common technique used to hinder analysis. In the instance of Agent Telsa, this capability is built-in to its builder tool (see beneath).
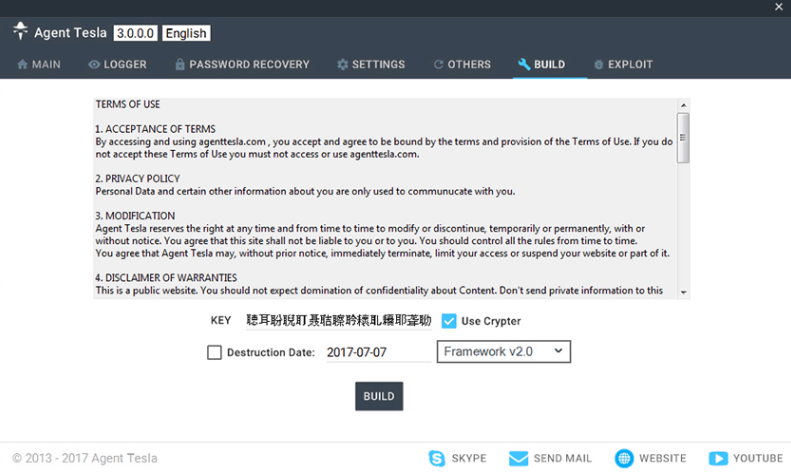
Effigy 3: Agent Tesla’due south built-in Crypter pick.
Tales from the crypt(er)
Of grade, not all malware has these sort of capabilities built-in and, as a issue, is far easier to detect without some method of packaging the malicious lawmaking for commitment.
I solution to this is to implement additional protection to the malware in the form of a crypter/wrapper/dropper (depending on the author and the finer details of its operation) which behaves in a similar fashion to the commencement and 2d stages of the Amanuensis Tesla malware discussed in a higher place.
Sleeping Beauty
Indeed, one of the Agent Tesla samples investigated (e977d1d55d4826011a6f585a6140168541ea5b86) took the belt-and-braces approach and was found to have two additional deployment layers beyond those exhibited past other samples.
While their relationship to Agent Tesla itself was initially unclear, these outer two crypter layers appear very closely related to an unnamed tool analysed past Hasherazade in July 2016 with pregnant sections of lawmaking (eastward.g. the lawmaking inside the 2nd layer that handles launching what the wrapper considers to be its last payload) near identical (see below).
Working backwards from decompiled, obfuscated code to identify which ane of dozens of available crypters was used is a significant (and typically non especially useful) attempt. Every bit a consequence, this crypter was nicknamed ‘Sleeping Beauty’ during Forcepoint Security Labs’ investigation after a string found in i of the obfuscation layers.
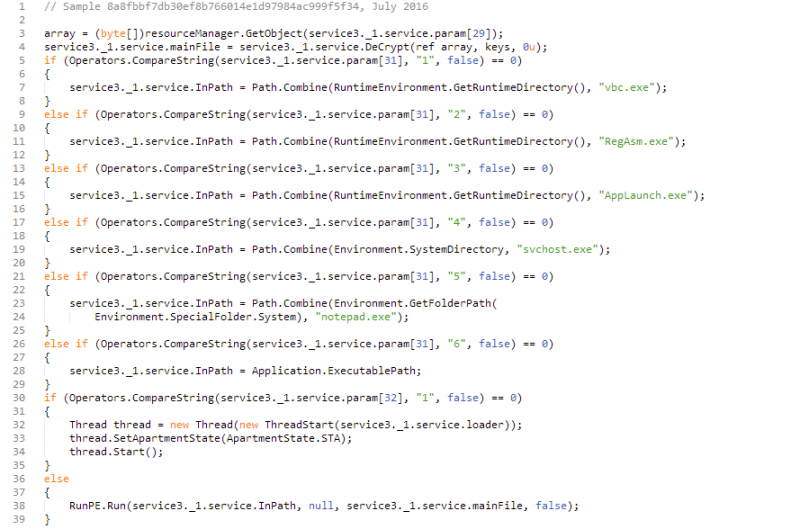
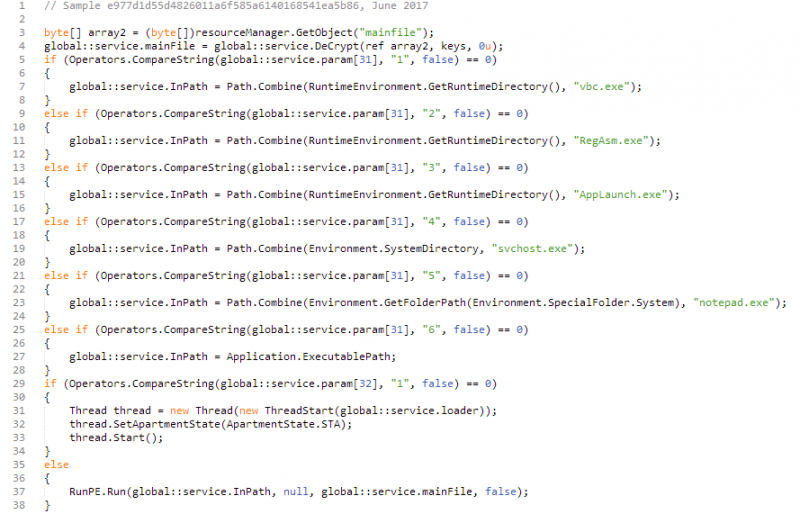
Effigy 4: Comparison of RunPE code from July 2016 and June 2017 ‘Sleeping Dazzler’ samples
Multiple small-scale variants of this tool accept since been found, but their behaviour is typical of architect-and-stub malware deployment tools:
- The initial stage (i.e. the stub) contains a ‘Resource’ section containing multiple elements (typically presented as a series of blobs in earlier samples and prototype files in later samples) which, when manipulated and combined correctly, produce a PE DLL file;
- This PE DLL file is executed without writing to the deejay and itself contains a ‘Resources’ section which tin exist unpacked to produce the final payload;
- The terminal payload is executed in a hollow process through the use of RunPE.
While RunPE itself is very ordinarily used, the presence of what appear to exist near identical implementations of the RunPE function telephone call (see to a higher place) potentially suggests a potent link between these samples.
A Crowded Market
In tardily July 2017, a further .Cyberspace wrapper/dropper sample was identified existence used to deliver the Predator Hurting keylogger.
Similar to the Sleeping Dazzler sample, this also appears to be self-obfuscating and use RunPE to run the malicious code, again with a very familiar looking ready of options for which procedure to hollow out:
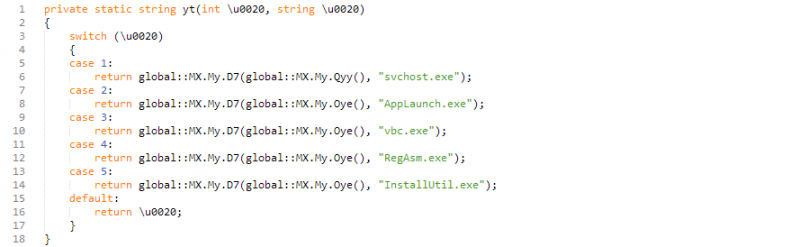
Figure 5: RunPE lawmaking inside crypter layer of Predator Pain sample.
There are, on the other paw, some very significant differences between this newer sample and the older
Sleeping Beauty
code: while
Sleeping Dazzler
followed a clearly divers ‘waterfall’ procedure of deployment, the functionality of the newer sample appears to be much more of a ‘mesh’, with the initial stub unpacking two DLLs which in turn apply a number of interdependent functions to decrypt and drop the payload stored in the original executable:
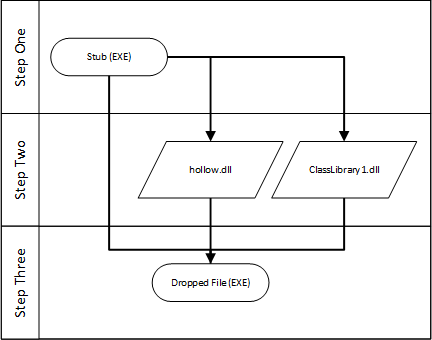
Figure 6: Deployment menstruation for crypter found dropping Predator Pain.
As such, without admission to the original source code of the crypter it is almost impossible to make up one’s mind whether or not this a new version of the (apparently quite quondam)
Sleeping Beauty, a tool that reuses a library or open-source code from
Sleeping Dazzler, or something completely different.
What is articulate, however, is the level of crowding in this particular market with Forcepoint Security Labs having found i repository alone containing the source code of nearly a hundred crypter variants.
Part Iii: The Criminal Overground.
Source: https://www.forcepoint.com/blog/x-labs/part-two-camouflage-netting
 RosyandBo.com Trusted Information and Education News Media
RosyandBo.com Trusted Information and Education News Media