In the wake of recent account compromises, including Associated Press and the rampant breaches orchestrated by the “Syrian Electronic Regular army”, Twitter take recently released 2FA (2 Gene Hallmark), which is a most welcome improver to bolster users’ security. It is not, nonetheless, the be-all and finish-all: users are even so responsible for choosing strong, hard-to-guess passwords. If your countersign is compromised, control of your account may be lost to malicious actors.
While it’s truthful that, given enough time and resources, all passwords are crackable regardless of their complication – a laissez passer-string of 200 random characters is ultimately just as vulnerable to brute forcing as a countersign containing simply one grapheme – the aim of a circuitous pass-string is to brand an attack temporally infeasible. Allow’s first take a wait at the total number of possible combinations for a given base of operations of elements:
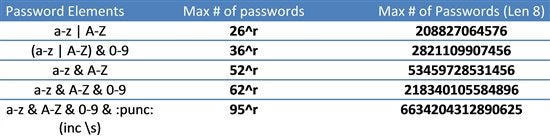
This tabular array encompasses repeating characters and is discipline to lexicality (ordering).
Of class, the first row contains all possible words in the English language, up to 8 characters. This may seem an unattainable number of combinations, only with modern GPUs (Graphics Processing Units) able to calculate hashes at a rate of up to 772 MH/south (772 million hashes per 2d) , the first row would be exhausted in around 270 seconds, or most 4.v minutes.
A user is unlikely to choose 8 capricious characters when creating a password that will be used on a daily basis; a typical string is likely to take some semantic content, such every bit a dictionary word (and various mutations thereof). Knowing this, crackers take produced many aids for this blazon of attack, including dictionary files and Rainbow tables – similar to dictionary files, just containing pre-computed hashes and the plaintext equivalent.
To requite an instance of how quickly weak passwords can be cracked, we set up a test using a simple Python script and Backtrack 5’southward Hydra combined with a moderate GPU, and targeted a test SMTP account:
Hydra v7.3 (c)2012 by van Hauser/THC & David Maciejak – for legal purposes only
Hydra (http://www.thc.org/thc-hydra) starting at 2013-05-23 07:08:12
……
login: ****** password: dave123
[VERBOSE] using SMTP LOGIN AUTH mechanism
i of 1 target successfully completed, ane valid password found
Hydra finished at 2013-05-23 07:08:51
<finished>
The password contained simply 36 possible chars: lower example a-z & 0-ix, and was cracked in 39 seconds.
While major sites volition accept (or should have) authentication attempt throttling, it’southward non uncommon for pocket-sized sites to allow unlimited attempts to access an account, which, coupled with password reuse, is a huge problem.
Users I have spoken to told me they use dissimilar passwords for different sites in almost all cases. When quizzed further, I found they typically used the aforementioned base string with some simple mutations, for example:
- countersign
- Countersign
- Passw0rd
- passw0rd!1
- pa$5w0rd!1
Knowing the base of operations cord, and with a very simple exchange (1337, symbols etc.) algorithm, we can crack these accounts in mere seconds. It’s lilliputian for an aggressor to automate this process, meaning accounts on some forgotten, compromised server can be obtained, leading to accounts with the same user name beingness attacked and possibly compromised.
As Twitter will attest, using secure, hard to guess pass-strings and varying user names (not always possible) are an absolute must for anybody who uses systems, applications, or sites accessible to others. Remember, it’s not just the internet that has people later your credentials; rogue employees and disgruntled exes, to proper name only two, are on the spotter for your details.
To ensure accounts are as secure every bit possible, it’s advisable to:
- Use strong, hard to guess, non-lexicon pass-strings. If the app doesn’t allow you to employ a mix of alphanumeric and special characters, you may not want the owner to have your details.
- Never, ever reuse passwords. It’s also proficient practise to non reuse passwords with simple substitutions.
- Ensure old accounts are deactivated where possible. Although you cannot trust a database would exist purged of credentials, it’s certainly a outset.
- Think before signing up to a site or service; always read their security policy.
- Be vigilant! Phishing is an easy-win for cyber criminals, so don’t give them an easy ride – sites and services will (or should) _never_ ask for your countersign via email.
Constant by these rules will assistance brand passwords as secure as they can be.
Source: https://www.forcepoint.com/blog/x-labs/twitter-adopt-2fa-here-what-you-can-do
 RosyandBo.com Trusted Information and Education News Media
RosyandBo.com Trusted Information and Education News Media