Privacy matters, it is a fundamental human right, and once you go down the Bitcoin rabbit hole, you realize how important it is to sacrifice a little convenience for improve protection of your wealth and identity.
This article will guide you through the best practices and tools to buy BTC anonymously while developing a case for more than privacy and security through documentation of emblematic events and the importance of protecting personal data.
To facilitate the path to more anonymity, we’ve structured this article into three distinct sections:
This guide has a shared focus on privacy and security, as the 2 go manus in hand. If you are a victim of a KYC info hack, yous volition rely on your security setup to keep your Bitcoin secure.
Although the communication provided in this article is well researched and well founded. We ask that you have the data independent therein as guidance and not as a directive. Nothing that we tin write can e’er exist a substitute to doing your own research.
Section 1: Why does privacy thing?
With the advent of the cyberspace, our privacy has faced profound challenges since our personal information is frequently at the mercy of malicious actors. It is our duty, and in our interest, to make sure that we have all available steps to protect our data.
You don’t need to live nether an authoritarian government to risk existence persecuted, distressed by the tax potency, or suffering wealth confiscation. Know your customer (KYC) and anti-money laundering (AML) regulations transcend the nature of a regime when our information is stored in online databases that are constantly exposed to hackers.
Databases have been and will be hacked, assuasive organized criminal offense to steal our data. Identity appropriation, credit card cloning, and bank details theft are but a few risks we constantly encounter. Another reason to avoid KYC-compliant platforms is that they could be in a position to take to reveal personal data to government in sure circumstances, such equally in the instance of the Celsius bankruptcy filing.
When you ain a unique nugget similar Bitcoin and betrayal your data, y’all risk compromising your wealth, which might mean everything to you and your family. Furthermore, the data can be cross-referenced with other hacked databases (such equally Facebook or Linkedin) to create a complete profile of a potential victim (email, proper name, address, BTC, etc.).
The even so brusque history of the cryptocurrency manufacture has uncovered many hacks, even breaching companies’ systems that claimed to be extremely safe.
Then, you should assume that no exchange or platform is secure enough, and take full responsibility for adopting the proper measures to protect your wealth. Nobody else will do it for y’all if yous don’t do it.
Buying Bitcoin anonymously is less frightening and burdensome than you might think, and information technology’s completely legitimate other than your fundamental right. If you recollect you lot’re breaking the police or doing something unethical, you lot could non be farther away from the truth.
Is Bitcoin anonymous?
No, Bitcoin is not anonymous, but it greatly depends on your employ. While Bitcoin represents monetary liberty, it’s also an open ledger, meaning that all transactions verified and added to the blockchain are visible to anybody.
The ledger doesn’t comprise any possessor’s data, such as a proper name and accost. However, an increasing number of analytics companies are running their own nodes in an effort to capture data such as your IP address. From in that location, the road to identifying you is short.
Bitcoin therefore is proving very advantageous to law enforcement, which can be a good thing when capturing bad actors or recovering stolen Bitcoin, like in the example of the Bitfinex hackers. However, with the justification that authorities need to tackle money laundering, terrorism, and illicit operations, such a surveillant system may affect the smaller genuine retail investor heavily.
Bitcoin privacy is increasing via upgrades such as Taproot, Taro, and ZK-Snarks. While Bitcoin is becoming more private, the onus remains on individuals to keep their coins safe and private by avoiding KYC and AML procedures.
What are KYC & AML
Know Your Customer or KYC is merely identity verification of a client carried out by a fiscal establishment to comply with regime regulations. Information technology may vary depending on the jurisdiction; however, most identification methods are like across the board, and these include:
- A valid ID carte;
- name;
- email accost;
- telephone number;
- utility bills to prove a domicile address.
Traders must accept exchanges’ stricter KYC procedures if they want to transact higher volumes. Such procedures include:
- A user’s photo;
- a selfie holding a piece of paper displaying further information;
- a video where you follow basic instructions to provide a 3d view of your caput.
Major crypto exchanges prefer to remain anti-money laundering (AML) compliant equally it helps them avert being liable when a user gets away with committing a crime because they failed to practice due diligence.
The information you provide to buy KYC’d Bitcoin may be used in the following ways:
- to trace your transactions and balances through Chainanalysis;
- place the wallet you lot engage and transact with;
- monitor how y’all buy Bitcoin;
- block you from using regulated services like in Canada;
- to confiscate your Bitcoin and make tax claims confronting you.
KYC is part of a more comprehensive regulatory measure identified as anti-money laundering (AML) to make it more hard for a criminal or terrorist arrangement to hide its illicit activities.
However, such regulations defeat the purpose of Bitcoin because they forbid one of the fundamental concepts of cryptocurrency: decentralization.
Past providing your data to a centralized entity similar an exchange, the pursuit of decentralization and anonymity recedes while the security of your asset is at run a risk. Fifty-fifty though near cryptocurrency exchanges pledge to provide maximum protection through robust military machine-style standards, you lot should never assume they are flawless, and your information may exist leaked.
Furthermore, you fall prey to assay companies that could be in a position to supply your data to third parties and governments.
Is it possible to un-KYC yourself?
Once you submit KYC data, this remains on official tape forever and cannot be removed. In that location are ways to mitigate the impact of such compliance, such every bit emptying your tape past selling your Bitcoin and repurchasing information technology with no verification to start afresh.
However, this will trigger a taxable event if yous sell for a profit unless you live in a Bitcoin-friendly jurisdiction that doesn’t taxation crypto holdings. You tin can also accept that your existing Bitcoin is KYC’d and motion on, knowing that in the time to come, you can purchase it in a KYC-free mode.
If you lot want to sell your Bitcoin and repurchase information technology anonymously, please go on reading to larn how you tin can avoid KYC.
Frequently Asked Questions
1. How tin I buy Bitcoin without verification?
In-person using cash, decentralized peer-to-peer exchanges, and selected ATMs are all good ways to purchase Bitcoin without verification. This guide volition help y’all detect the nigh suitable ways to do it.
two. Can I buy Bitcoin with a debit card with no verification?
Debit Cards are typically an extension of your bank account, which would exist fully compliant with KYC. It is possible to add a few actress layers of obfuscation through coin transfer services which you can read about below.
Pre-paid or virtual debit cards for online purchases offer softer verification requirements than a typical depository financial institution carte du jour. However, they are never entirely anonymous since they are reloadable.
3. Can I buy Bitcoin with a credit card with no verification?
Similar to debit cards, soft-KYC pre-paid and virtual credit carte du jour options exist. Many payment circuits like Visa and Mastercard offer prepaid credit menu payments through automated services like Ezzocard or Mistiness.
4. Is Bitcoin more traceable than cash?
Yes. Bitcoin is more traceable than greenbacks. Too appearing in an open ledger available for everyone to see, Bitcoin addresses are “pseudonymous,” meaning they don’t automatically reveal their owner’s identity. If it is used on an substitution that implements KYC, it may be easily linked to a real-earth identity depriving privacy.
5. How can Bitcoin be tracked?
Unlike common belief, Bitcoin transactions are highly traceable because they are stored in a public, transparent blockchain, a distributed ledger visible to everyone. Block explorers that track every blockchain transaction are becoming increasingly sophisticated, making Bitcoin addresses, cake numbers, and transaction hashes easier to trace.
When coupled with wallet explorers, such tools make it possible to draw connections between addresses and the wallets used to hold Bitcoin.
Section 2: Steps to protect your privacy
Buying Bitcoin anonymously can be challenging, only it’due south possible if we purchase with cash in person or through a KYC-complimentary ATM. We can too choose KYC-gratis or soft-KYC exchanges, especially if they back up mixers –nosotros’ll go through more on this later.
Unfortunately, the convenience of ownership Bitcoin through centralized KYC-compliant exchanges and Fintech comes with a price, and that’s your privacy. Still, if you lot are set to trade convenience for more privacy, at that place are ways to go well-nigh information technology, and we’ll become through what they are.
Such methods shouldn’t exist intimidating and only require some of your time to dig down some privacy and security steps, from online protection to transaction safety. You won’t need to apply all the options detailed beneath, but adopting some of them will go a long way to give you more peace of heed.
It goes without saying that few things in life are unassailable. Any number of the post-obit solutions can be compromised in the futurity, then best practice would be to understand what each option solves and to combine those that brand almost sense to keep your identity individual.
A guiding principle

If you want to keep your coins private, the first step is to never reveal to people that you own Bitcoin, particularly how much you lot concur, as this will make y’all a target for malicious actors.
Connecting to the net
Use a dedicated estimator or phone
You should e’er assume your Bitcoin is at take a chance online and could be compromised by hackers who could exploit vulnerabilities. You lot must prevent these vulnerabilities and avoid mixing your general internet employ with your Bitcoin wallets and activities.
Nosotros always recall we are smarter than hackers, but scams, primarily through phishing, get increasingly sophisticated, so it’southward better to provide max privacy and security to avoid all chances. A Bitcoin-merely dedicated automobile is the best mode to avoid being tricked into scams using malicious websites and programs.
When choosing your Bitcoin-defended machine, it would be helpful to keep the following advice in mind:
- The worst operating system is Windows considering its security is notoriously weak and more exposed to keyloggers, viruses, etc.;
- Information technology’south meliorate to employ either IOS or Linux as their security standards are amend than windows;
- The best OS is TAILS (The Amnesic Incognito Live Organization), a security-focused Linux distribution of free and open software that connects to the Internet exclusively through the anonymity network Tor.
- Bonus: Encrypt your computer and/or telephone with PGP encryption to increase security and so that any sensitive information that you may or may not agree on these devices cannot exist recovered past anyone without the key that you privately hold.
Web browsers
While Chrome is past far the well-nigh popular browser in the world, there are alternative browsers that are more respectful of privacy. In 2020, Mozilla emulated a 2009-2011 report from security practiced Dr. Lukasz Olejnik using 52,000 Firefox users. Mozilla’due south study confirmed Olejnik’s earlier findings that companies such as Google and Facebook are able to track people based on their browsing histories using a method known as re-identification.
Absolutely, it’south unlikely that this is a risk that will bear upon as well many people. Nonetheless, using an alternative browser to Chrome is a simple solution.
- Tor Browser is a favorite of Edward Snowden. Tor sets the standard for avoiding fingerprinting. It prevents unauthorized snooping with the help of its subconscious relay servers and encrypts your traffic three times for three dissimilar decentralized nodes.
- Mozilla Firefox is quite secure. It offers a private browsing manner, including popular-up blocking, malware and phishing protection, and tracking. It has likewise borrowed Tor techniques to block browser fingerprinting.
- Epic is a powerful privacy-axial web browser that uses DuckDuckGo as its default search engine. Its mission is to deliver “farthermost privacy” and does so by blocking cookies, ads, and data-tracking spider web analytics systems. It also doesn’t permit plugins, doesn’t use auto-suggest or spell-checks, or other such enhancements.
- Brave is a complimentary and open-source Chromium-based spider web browser that claims to be blocking ads, fingerprinting, scripts, and advertizing trackers by default. However, information technology has been reported to exist misusing affiliate links for profit, besides actually storing your information if you opt for their rewards program. By being rewarded, you are actually selling your data to them.
- Impervious.ai is a newly released Peer-to-Peer spider web browser that uses Decentralized Identifiers (DIDs) to let users to cryptographically command their identity and designate how they’d like to exchange data online. They promote encrypted messaging, video calls, and certificate sharing. It utilizes both peer relays and the Bitcoin Lightning Network to establish real-fourth dimension, cryptographically-secure information transmission channels.
Bonus tip: Resist the urge to install browser plugins on these browsers, every bit they invariably reduce your privacy.
Block spider web trackers
Spider web tracking websites collect, store and share information nigh visitors’ online activities. Potentially a web tracker could link 2 purchases belonging to the same user to the Bitcoin blockchain’southward transactions, thereby identifying an unabridged cluster of addresses and transactions.
Blocking web trackers is possible through the post-obit providers, which are a nifty manner of navigating online more than securely and privately.
- uBlock Origin, a free and open-source browser extension for content filtering, including ad-blocking;
- Adblock Plus, a software that blocks and filters ads;
- Ghostery is a free, open-source privacy and security-related browser extension and mobile application.
Use a VPN
Virtual individual networks (VPNs) are services that protect your internet connection and privacy online. They typically create encrypted tunnels for your data, protect your online identity by hiding your IP address, and allow you to use public Wi-Fi hotspots safely.
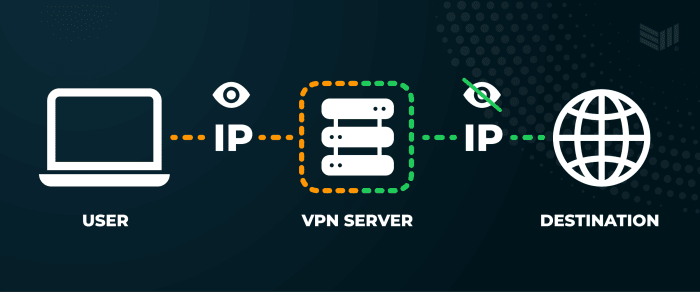
Some prominent VPN services are NordVPN, Proton, and ExpressVPN. Information technology’s enough to subscribe to their services to enjoy more privacy online. Costs are commonly betwixt $3.99 and $six.99 per month.
Use TOR
The onion router (TOR) is a globally distributed network of individual volunteer servers used to ensure anonymous communication. Its decentralization makes information technology difficult to notice its encrypted connections.
The deviation with a VPN is their operation method. While TOR encrypts and makes your online traffic private through a decentralized network, VPN encrypts and routes your connection using a network of servers maintained by a centralized entity.
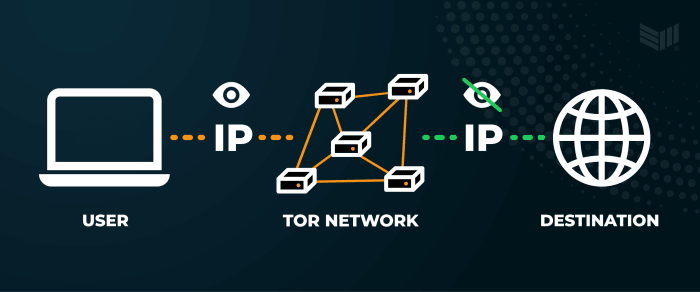
They both raise your online security and privacy; all the same, TOR is similar to Bitcoin by not having a single bespeak of failure, while VPN has all the characteristics of a centralized entity. TOR’due south decentralization will be more effective if more than people run their ain TOR node; therefore, likewise running your Bitcoin node, it would be beneficial for the system to run your own TOR node likewise.
Run a total node
Running your own node protects your Bitcoin wallet from disclosing data most your transactions. You might wonder why since your Bitcoin wallet should exist private, especially a non-custodial ane.
Random public nodes verify your Bitcoin transactions if you lot don’t run your own node. A random node operator could be a surveillance company that could access your IP accost (that tin be used to place you lot) and all of your Bitcoin wallet residue, exposing it to governments or hackers’ potential interference if it gets leaked.
Information technology so becomes clear why running your ain node will protect y’all from third parties, similar block explorers, that could leak your information. As computer scientist Nick Szabo defined them, such “trusted 3rd parties are security holes” that should be removed for more than privacy and security past running your own node.
A node run through TOR, a VPN, or both in tandem, attains further enhanced protection. Therefore, using them is highly recommended.
Setting up your ain node is relatively elementary and beneficial to the overall network robustness.
Here are a few options available to run your own node deeply:
- Bitcoin cadre is the open-source software that connects a user to the Bitcoin peer-to-peer network to download and fully validate blocks and transactions;
- DIY options requite you the maximum cocky-sovereign Bitcoin y’all could ever take. Running your DIY node tin can be achieved with a few hundred dollars of hardware and will offering you that ultimate privacy and security you lot deserve as a Bitcoin enthusiast. Raspiblitz, Start9, Umbrel, and Voltage are a few node providers that y’all can use for your DIY node;
- Plug n Play any of the node providers listed above, including Nodl, RaspiBlitz, and The Bitcoin Machine, and you’re fix to go. All you have to practise is larn the relevant hardware and plug it in, and it really is that simple. You are just ii steps away from your best privacy and security practices.
No affair which method or hardware yous choose to run your ain node, we tin can never stress enough how important it is to undertake this process. Verifying your ain balance and transactions, other than contributing to the expansion and security of the Bitcoin network, will accrue the sense of freedom and self-sovereign Bitcoin was created for.
Registering on platforms
Avert services that require yous to register with your easily identifiable KYC information, like your proper noun, address, email, and phone number.
Bypass electronic mail verification
It is possible to annals an anonymous email accost, non tied to your personal information and is preferably defended to the procedure of ownership Bitcoin simply. This will end you from being exposed to other users, possible phishing emails, and, overall, being recognized.
Services similar Protonmail and Tutanota were created to preserve your privacy and security; therefore, you should consider adopting such tools.
Bypass phone verification
Just like for emails, you could obtain a telephone number that’s not tied to your identity. The following practices and tools will help you achieve it:
- Purchase a burner phone, a cheap mobile phone designed for temporary use, after which it may be dumped. Burners are purchased with prepaid minutes and without a contract.
- Buy an anonymous sim such as one provided past silent.link that you can pay with Bitcoin without any KYC info.
- Use online sim verification services such equally Text Verified, and Receive SMS to bypass verification. These services can be useful for i-off purchases and are liable to fail for multiple verifications.
Sending fiat money
Unless you use other cryptocurrencies to buy Bitcoin or exchange it for appurtenances and services, you’ll demand fiat money to execute the purchase. Sending coin online typically leaves a clear trace of your personal information, including your proper noun and address, the amount transacted, the date and time, and your bank business relationship details.
These details move from your banking company business relationship to the exchange or banker you employ for the transaction. If this is your preferred method of buying Bitcoin, you can yet avoid leaving an irreversible trace, and listed below are some ways to go well-nigh it.
Use Prepaid cards
You lot can circumvent the tracking of your money linked to your data by purchasing pre-paid cards, such as gift cards, that many KYC-free platforms accept.
If you have the hazard to purchase prepaid cards from your local store in cash instead of your debit/credit card, you’ll reach the ultimate level of anonymity for such a method.
- Prepaid Bitcoin vouchers are a fast-rising mode of buying Bitcoin considering they are simple and require no KYC. Pop prepaid Bitcoin vouchers are Azteco and 1ForYou. Bitcoinbons is some other provider available across 4,000 tobacconists and petrol stations in Austria.
- Prepaid debit cards are usually linked to a banking concern account and a verifiable individual. However, information technology’s possible to get prepaid debit cards in some countries that don’t require identifying information. Virtual debit cards are quickly expanding every bit KYC-gratis payment methods. Local Bitcoins & Paxful are Bitcoin exchanges that have prepaid debit cards.
- Prepaid souvenir cards – Prepaid souvenir cards tin exist used to buy Bitcoin on many exchanges. Paxful accepts almost of them, including Flexevoucher, Amazon Gift Cards, Steam Wallet Gift Cards, PlayStation Network, and XBOX Souvenir Cards, to proper name a few. Hodl Hodl also provides many gift card options, while Robosats accepts Amazon eGift cards. Gift cards would preferably be purchased using cash.
Money transfer services
While most Bitcoin exchanges approve of the same payment methods in most countries, including gift cards and prepaid cards, depending on your jurisdiction, you might have to resort to sending a wire or using one of the following services anonymously:
- With Moneygram, for instance, yous can use an email account with a masked name and address and a prepaid or virtual credit menu, which are safe means to avoid revealing your information.
- Paypal Business and Premier accounts allow you to create an account using fictitious personal data to transport fast payments. Merely add your recipient’due south email address to your list of payees, and you are fix to send money online anonymously.
Afterward purchase
Labeling
Addresses and transactions are inherently continued in the Bitcoin blockchain, making it relatively easy to extract private information. To avoid privacy leaks, coin control and labeling become necessary for more than anonymous transactions.
Just like physical coins in your day-to-day fiat cash wallet, when you spend your Bitcoin, y’all select your wallet’s coins to spend, known as Unspent Transaction Outputs (UTXO).
Assuming your coins go tracked down by observers when you spend or receive them, labeling might come in handy as it will help you decide to whom to send the selected Bitcoin and from whom y’all receive it.
By recognizing them through labels, yous can avoid re-using them by keeping them individual from entities or individuals and using new coins then they cannot be tracked down.
Coin Mixing / Joining
In the ‘Run a full node’ section, we mentioned the importance of verifying your own transactions to keep your coins private. If you don’t run your node, your wallet and IP addresses are exposed to the potential surveillance of a random node that could leak your data.
This is where coin mixing and joining come to the rescue. With greenbacks, if user A pays user B with a ten-dollar nib, user B has no idea where that beak came from. With Bitcoin, coins are more hands traceable, a fleck like revealing on a neb the names of all previous users and the amounts transacted.
Coin Mixers

Money mixers are software and service solutions that allow users to mix their coins with others, disguising the ties between their addresses and existent-world identity, thereby preserving their privacy.
This concept is straightforward: users transport coins to the mixer, and the mixer sends different coins back – normally minus a mixing fee.
When mixers are centralized services, they are inevitably vulnerable and present flaws every bit being a single signal of failure they are exposed to malicious attacks. Trust is another weakness, as the services must exist trusted to transport the coins back and non steal them from the user.
Mixers must also be trusted to preserve your privacy, as they know exactly which coins were exchanged and could determine the transactions’ trail. The alternative solution to trusting centralized mixers is to employ CoinJoin.
CoinJoin

CoinJoin provides anonymity to Bitcoin users when they transact with each other, obscuring the sources and destinations of the BTC used in transactions. This method works by combining several payments from different users into a unmarried big transaction, mixing their UTXO in a pool, thus making information technology unclear who sent bitcoin to whom.
Bitcoin developer Gregory Maxwell outset developed CoinJoin in 2013, and early on examples included Dark Wallet, JoinMarket, and SharedCoins. Joinmarket is all the same a leading project that allows users to create wallets and send coinjoin within the aforementioned application.
Early decentralized solutions included Coinmux, Coinjumble, and CoinJoiner; however, none of these were widely used and, therefore, non very helpful since the concept makes sense just when at that place’s someone to bring together forces with.
Later efforts include Wasabi Wallet and Whirlpool from Samourai Wallet. Wasabi wallet and hardware wallet Trezor are combining efforts to offer coinjoin for users’ enhanced privacy and program to offering a coinjoin mixing scheme next year.
PayJoin is an interesting coinjoin protocol that further obfuscates the buying of UTXO during a coinjoin transaction mixing cycle where both the sender and the receiver coordinate to build a single Bitcoin transaction, thus masking the payment amount. Not-custodial Bitcoin and Lightning wallet Blue Wallet added support for Payjoin at the end of 2020 to further raise its wallet users’ privacy.
Avert Cake Explorers
Block explorers are software that elaborates information from the blockchain to provide network statistics and permit users to look up specific addresses, transactions, or blocks through a simple search bar. They are likewise used to obtain more data for block assay companies like Chainanalysis and tin can reveal how much Bitcoin you concur and your transaction history.
If you are running your own node, using cake explorers is more than private than using online versions.
Wallets
Afterwards purchase, transfer your Bitcoin to a non-custodial wallet for more privacy. Cold storage, or hardware wallets, are preferred as they operate offline, reducing the risk of malicious attacks.
Wallets are typically anonymous because no KYC procedures are required to open one unless they too role every bit exchanges. In that case, they might need some form of verification, and you might desire to use it for day-to-24-hour interval transactions while keeping a different one to shop your stack more than privately and securely. You should too connect your wallet to your own node for extra privacy and security.
HD Wallets are hierarchical deterministic (HD) wallets that prevent you from reusing an address you used in the past to receive bitcoin past generating multiple keys (addresses) from 1 unmarried private key. Each of those keys can generate its own set of keys and and then on to an infinite number of series. It’southward advised to have advantage of this feature.
Multi-signature (Multisig) wallets provide extra security past requiring more than than i signature (central) to authorize a Bitcoin transaction and dividing up responsibleness for the possession of bitcoins. Y’all should e’er use a multisig with your own node to avert KYC trade-offs with popular Casa & Unchained Capital apps, for instance.
Seeds are probably the virtually critical component of your wallet feel as they should always be stored safely, for example, in a well-subconscious piece of paper, in encrypted methods, or on a steel plate.
Section 3: Where to buy Bitcoin Anonymously
You lot now have a few all-time practices bachelor to enhance your security and privacy when buying Bitcoin, and you can employ them with the following methods for more anonymity. Not all privacy steps are necessary for each of these methods. You can apply your judgment and capabilities to adopt at least a few to give you lot more peace of mind.
Buy locally (in person)
Ownership locally and in person used to exist more than mutual when the value of Bitcoin was much lower than today, and people took risks associated with trusting the buyer or the seller.
Still, if the counterpart is someone you lot trust reasonably, information technology’d still represent an excellent way to buy Bitcoin. It’s even meliorate if the transaction is washed with greenbacks, as only the other entity would know about the operation, reducing the risk of being tracked downwardly by authorities or malicious actors to near cipher.
Buy locally (concrete stores)
Likewise online, Bitcoin can too exist acquired in concrete stores, commonly a foreign commutation store with a little kiosk with Bitcoin-dedicated buyers and sellers. Many require some class of ID, but that typically depends on the land’s store location.
This is an splendid option to buy Bitcoin with a KYC-free procedure; however, buyers should exist enlightened of the hazard of being physically seen and therefore associated with Bitcoin by criminals.
Here are a few locations effectually the world where Bitcoin can be bought with no verification required:
- The Bitcoin Store has 3 locations in Croatia – Split, Zagreb & Rijeka– where you can purchase 15,000 HRK (approx 2,000 euros/dollars) without using an ID, then long as y’all are over xviii.
- The Business firm of Nakamoto is located in Vienna, Austria. The maximum purchase immune without ID is €250.
- LibertyX is America’due south first and largest network of Bitcoin ATMs, cashiers, and kiosks. Depending on the location, yous can buy up to $i,400/week (rolling seven days) with only a telephone number.
ATMs / BTMs
Automatic teller machines (ATMs) where y’all tin purchase bitcoin are as well chosen Bitcoin teller machines (BTMs). ATMs are known for withdrawing fiat currencies from depository financial institution accounts. In dissimilarity, BTMs use blockchain to execute transactions that send the cryptocurrency to the user’s wallet through a QR code.
Ownership Bitcoin with an ATM is quick and often KYC-gratis. Still, the transaction fees are loftier, from 8 to xx%, due to the loftier maintenance costs of the hardware.
There are currently around 39,000 ATMs spread beyond 79 countries. The U.s.a. is where they are primarily distributed; notwithstanding, they are rising fast everywhere. If yous visit Coin ATM Radar, you lot tin can detect an ATM most you lot, including the types of KYC requirements.
Crypto exchanges & apps
Exchanges are typically the nearly convenient and easiest way for people to buy Bitcoin, and they can exist either centralized (CEXs) or decentralized (DEXs). Buying Bitcoin on exchanges is convenient, only that convenience oftentimes comes with a price, your privacy, and security.
Decentralized (DEX)
Using DEXs is usually recommended to protect your privacy due to their decentralized nature and fewer KYC requirements. Using specific payment methods to receive your funds is all the same necessary to maintain complete privacy, equally sending straight from your KYC’d banking company business relationship obviously leaves a transaction trail.
- Bisq is a decentralized peer-to-peer substitution that allows anyone to purchase and sell bitcoin in exchange for fiat currencies and other cryptocurrencies. It is gratis software with no centrally-controlled servers and no unmarried points of failure. It offers different types of payments, including face-to-face and cash, making it an ideal KYC-costless solution.
- Robosats is a peer-to-peer Bitcoin non-custodial substitution ideal for onboarding new users as it’s easy and quick to utilise. It requires no KYC since information technology’s based on pseudonymous avatars that allow customers to merchandise Bitcoin over the Lightning Network using the TOR browser only.
- Hodl Hodl is a peer-to-peer Bitcoin non-custodial exchange that offers p2p lending services. It requires no KYC or AML procedures and offers many payment options, including cash in-person, prepaid debit cards, and bank transfers. It works through a multisig escrow where the seller controls ane of the keys and agrees to a payment method with the heir-apparent. In one case payment is received, the Bitcoin is released and sent to the buyer’s wallet.
- Paxful is a Bitcoin exchange and digital wallet that offers a broad range of payment methods, including gift cards, vouchers, and airline tickets. It ordinarily does non require KYC verification; however, it had to introduce it at the end of 2020 for a select number of countries.
- Peach is a peer-to-peer mobile app only that allows customers to buy and sell Bitcoin using amazon gift cards too. The service is however in beta mode, and there’south a waiting list to join it; even so, it is one of the few Bitcoin p2p marketplaces on a mobile application for the European market place.
- Local coin swap is a KYC-gratuitous peer-to-peer not-custodial exchange that uses escrow protection for users who tin can purchase and sell Bitcoin with several payment methods, including cash in-person, greenbacks by post, and gift cards for higher anonymity.
- Bitcoin.global is a p2p cryptocurrency commutation that requires no identity verification, no waiting times, and no additional charges, just an email address to go you lot started.
- Telegram, in April, revived an abandoned blockchain project called Wallet Bot that allowed users to buy Bitcoin. They have recently launched a peer-to-peer cryptocurrency substitution that users can join to transport crypto via chat messages, with but a telephone number required for verification.
You can visit a complete list of p2p decentralized exchanges that crave very little or no KYC on GitHub.
Centralized (CEX)
When you purchase Bitcoin on a centralized exchange, you expose your data to leaks and hacks and may be at hazard. Not just is your online identity at risk, merely your physical self is as well challenged.
Depending on your jurisdiction, CEXs might yet be an selection to buy Bitcoin with piddling verification if they tin resist strict KYC regulations. However, due to their nature, they might not be able to ensure soft- or no-KYC forever.
- Relai is based in Switzerland and is Europe’due south near accessible bitcoin-only investment app. It enables instant Bitcoin purchases with no eolith, registration, or strict KYC process. The Relai app simply provides non-custodial wallets, pregnant its customers maintain control of their individual keys at all times
- Bybit is a cryptocurrency exchange and a fintech platform that offers a p2p version that accepts over 300 payment methods, including greenbacks in-person. It requires soft KYC procedures based on trading and withdrawal levels. Users can withdraw upwardly to 2BTC with no verification required.
- Damecoins is a cryptocurrency exchange where users tin purchase Bitcoin with no verification and ID needed upwardly to $l,000 transacted, except an electronic mail address to receive confirmation of purchases and account information. They also accept souvenir cards and bank transfers for transactions over $ten,000 upon request.
Earn Bitcoin equally income
The growing Bitcoin industry offers many opportunities to those who want to get a task that pays in BTC. You’ll still need to apply the security and privacy measures highlighted in this guide to receive Bitcoin anonymously. Withal, if yous combine getting paid in BTC with moving to a crypto-friendly jurisdiction, you might exist able to earn Bitcoin tax-gratuitous besides.
Become a solo miner
Another way to acquire Bitcoin with no KYC is to start solo mining or mining at home. You can read nigh this subject in our extensive guides on Bitcoin mining and how to mine Bitcoin at domicile.
Operate a Lightning node
Yous can stack sats anonymously operating a Lightning node by charging fees to process transactions through your Lightning channels. Running a lightning node won’t earn you much Bitcoin at this point in time, but it would still be an excellent way to proceeds modest amounts of BTC while saving on payment fees and helping secure and grow the network.
SUMMARY
Despite its reputation, Bitcoin is not entirely anonymous. Authorities want you to believe that it is a safe oasis for criminals, coin launderers, terrorists, and tax evaders; however, the reality is that information technology’due south much more traceable than cash and digital payments due to its immutable and transparent open up ledger.
It’s more than convenient and cheaper to reveal your identity to buy Bitcoin; however, yous should consider the trade-offs because more privacy might stop you from making costly mistakes in the long term.
Privacy takes work. But it’s worth information technology.
Source: https://bitcoinmagazine.com/guides/how-to-buy-bitcoin-anonymously
 RosyandBo.com Trusted Information and Education News Media
RosyandBo.com Trusted Information and Education News Media